In this Opencart tips and tricks, we are showing you 25 Opencart security tactics to make Opencart’s website secure by providing a cheat sheet for Opencart eCommerce users, so that the customers can buy products confidently which may increase your conversion rates. Here are the 25 lists of things that you can do to make the Opencart website secure:
Use good and secure hosting
Research and buy good, reliable, and secure hosting.
Check if the install/ folder is still there
Once Opencart is installed, you need to remove/delete the install/ folder. Renaming the folder will also have a security hole. Thus, always delete the install/ folder.
Proper Security settings in the admin
Login to the admin section >> System >> Settings >> Edit required store >> then in the Server tab, select the use SSL to Yes
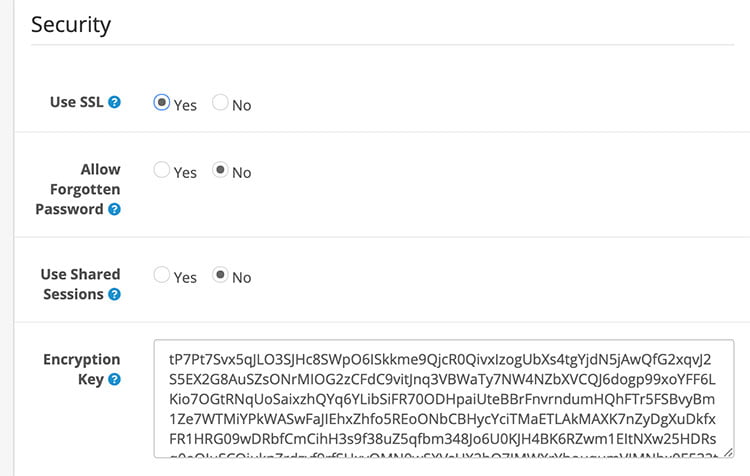
Use SSL: To use SSL check with your host if an SSL certificate is installed and add the SSL URL to the catalog and admin config files.
Allow Forgotten Password: Allow forgotten passwords to be used for the admin. This will be disabled automatically if the system detects a hack attempt.
Use Shared Sessions: Try to share the session cookie between stores so the cart can be passed between different domains.
Encryption Key: Please provide a secret key that will be used to encrypt private information when processing orders.
Use HTTPS/SSL Certificate
Selecting SSL to Yes on the above setting will not give you an HTTPS URL, your server also need to have SSL installed. Nowadays most servers provide free encrypt SSL certificates which can be setups with just some clicks, or you can use more secure SSL certificates.
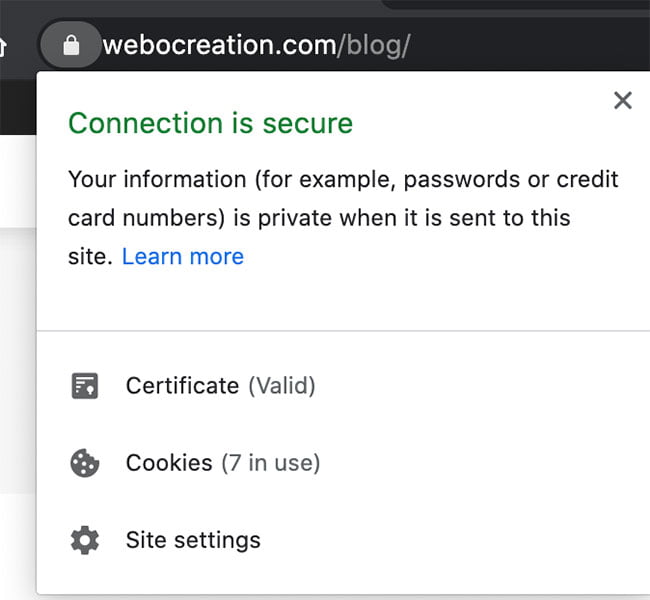
One thing you need to take care of is all of your URL links need to start with HTTPS:// instead of HTTP:// else it will not be fully secured. If you are using external URLs, make sure they start with HTTPS://. With proper SSL installation, your URL will look like the below when you clicked on the SSL icon:
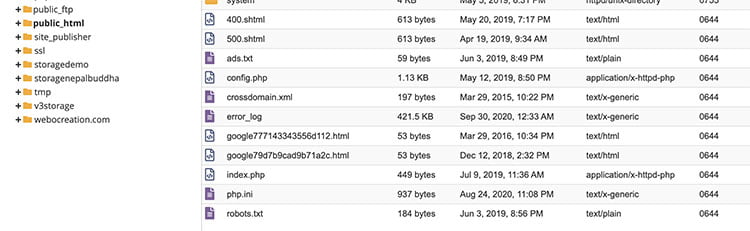
Protect your storage/ folder and other files like the config.php file and admin/config.php
Keep storage/ folder outside of the public_html folder. In the image below, my storage folder is v3storage. Similarly, check your file permission and keep it below 0644.
Use the latest PHP version
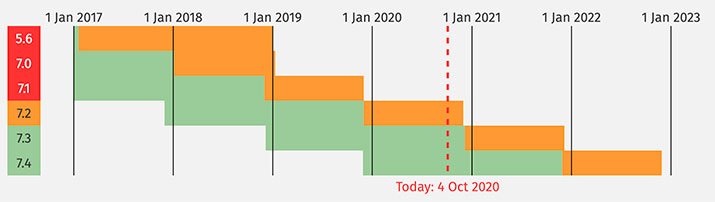
See the chart the PHP V5.6 is already at the end of its life which means there will be no update of security, and they are exposed to unpatched security vulnerabilities. So for security always use the latest version of PHP.
Watch this session, on how the creator of PHP describes the performance in PHP 7. Performance always good impact.
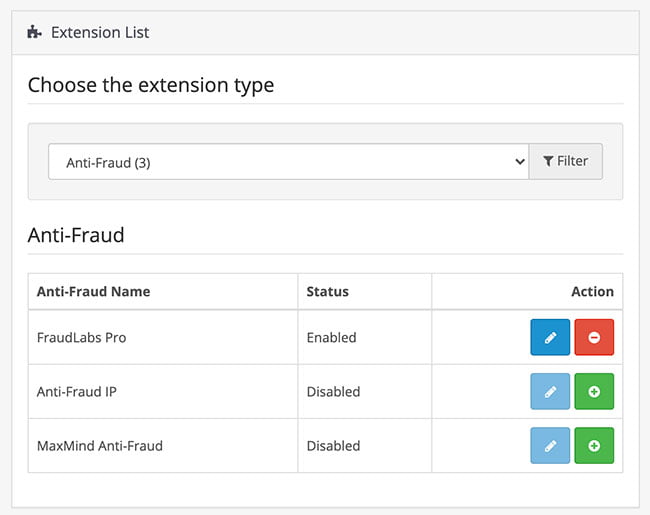
Use Anti-fraud extension
Opencart by default provides some Anti-fraud extensions, they help store owner to secure their online e-commerce website from malicious fraudsters and make it more secure. Login to admin >> Extensions >> Extensions >> Choose the extension type as Anti-Fraud >> then you will see lists of modules that you can use. You can use some of them for free like 500 queries/month.
Error handling setting
Enable error logging into the error.log file and it will insert into the database. It is a better idea not to display errors. If you display errors then it will show all full paths of files and it may help hackers. While you perform your debugging errors you can enable it but for security reasons keep it checked as No. You can set the error handling at admin >> System >> Settings >> edit Your Store >> Server tab and you will see the error handling section at the end.
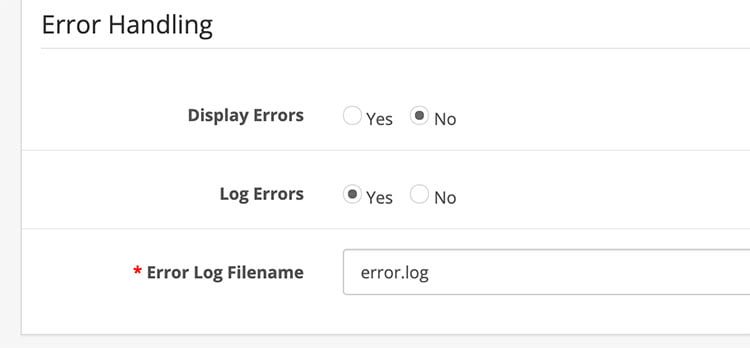
Monitor your admin error logs
Analyzing error logs also gives what issues are happening and fixing them is important. Similarly, check logs at admin >> Extensions >> Modifications >> Log tab. Fixing errors makes the site more secure.
Block bad bots
Opencart provides settings for Robots. You can get it at admin >> System >> Settings >> Edit Your Store >> Server tab and you can see the Robots field. A list of web crawler user agents that shared sessions will not be used with. Use separate lines for each user agent.
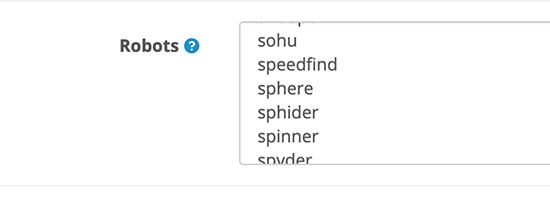
You can use the following:
abot dbot ebot hbot kbot lbot mbot nbot obot pbot rbot sbot tbot vbot ybot zbot bot. bot/ _bot .bot /bot -bot :bot (bot crawl slurp spider seek accoona acoon adressendeutschland ah-ha.com ahoy altavista ananzi anthill appie arachnophilia arale araneo aranha architext aretha arks asterias atlocal atn atomz augurfind backrub bannana_bot baypup bdfetch big brother biglotron bjaaland blackwidow blaiz blog blo. bloodhound boitho booch bradley butterfly calif cassandra ccubee cfetch charlotte churl cienciaficcion cmc collective comagent combine computingsite csci curl cusco daumoa deepindex delorie depspid deweb die blinde kuh digger ditto dmoz docomo download express dtaagent dwcp ebiness ebingbong e-collector ejupiter emacs-w3 search engine esther evliya celebi ezresult falcon felix ide ferret fetchrover fido findlinks fireball fish search fouineur funnelweb gazz gcreep genieknows getterroboplus geturl glx goforit golem grabber grapnel gralon griffon gromit grub gulliver hamahakki harvest havindex helix heritrix hku www octopus homerweb htdig html index html_analyzer htmlgobble hubater hyper-decontextualizer ia_archiver ibm_planetwide ichiro iconsurf iltrovatore image.kapsi.net imagelock incywincy indexer infobee informant ingrid inktomisearch.com inspector web intelliagent internet shinchakubin ip3000 iron33 israeli-search ivia jack jakarta javabee jetbot jumpstation katipo kdd-explorer kilroy knowledge kototoi kretrieve labelgrabber lachesis larbin legs libwww linkalarm link validator linkscan lockon lwp lycos magpie mantraagent mapoftheinternet marvin/ mattie mediafox mediapartners mercator merzscope microsoft url control minirank miva mj12 mnogosearch moget monster moose motor multitext muncher muscatferret mwd.search myweb najdi nameprotect nationaldirectory nazilla ncsa beta nec-meshexplorer nederland.zoek netcarta webmap engine netmechanic netresearchserver netscoop newscan-online nhse nokia6682/ nomad noyona nutch nzexplorer objectssearch occam omni open text openfind openintelligencedata orb search osis-project pack rat pageboy pagebull page_verifier panscient parasite partnersite patric pear. pegasus peregrinator pgp key agent phantom phpdig picosearch piltdownman pimptrain pinpoint pioneer piranha plumtreewebaccessor pogodak poirot pompos poppelsdorf poppi popular iconoclast psycheclone publisher python rambler raven search roach road runner roadhouse robbie robofox robozilla rules salty sbider scooter scoutjet scrubby search. searchprocess semanticdiscovery senrigan sg-scout shai'hulud shark shopwiki sidewinder sift silk simmany site searcher site valet sitetech-rover skymob.com sleek smartwit sna- snappy snooper sohu speedfind sphere sphider spinner spyder steeler/ suke suntek supersnooper surfnomore sven sygol szukacz tach black widow tarantula templeton /teoma t-h-u-n-d-e-r-s-t-o-n-e theophrastus titan titin tkwww toutatis t-rex tutorgig twiceler twisted ucsd udmsearch url check updated vagabondo valkyrie verticrawl victoria vision-search volcano voyager/ voyager-hc w3c_validator w3m2 w3mir walker wallpaper wanderer wauuu wavefire web core web hopper web wombat webbandit webcatcher webcopy webfoot weblayers weblinker weblog monitor webmirror webmonkey webquest webreaper websitepulse websnarf webstolperer webvac webwalk webwatch webwombat webzinger whizbang whowhere wild ferret worldlight wwwc wwwster xenu xget xift xirq yandex yanga yeti yodao zao zippp zyborg
You can set it in the .htaccess file like below as well, if you are using Nginx then you need to write code that returns 403 or so.
RewriteCond %{HTTP_USER_AGENT} ^.*(agent1|Wget|Catall Spider).*$ [NC]
RewriteRule .* - [F,L]
Allowed File extensions and allowed file mime types permissions
Opencart by default has options to restrict file extensions and file mime types.
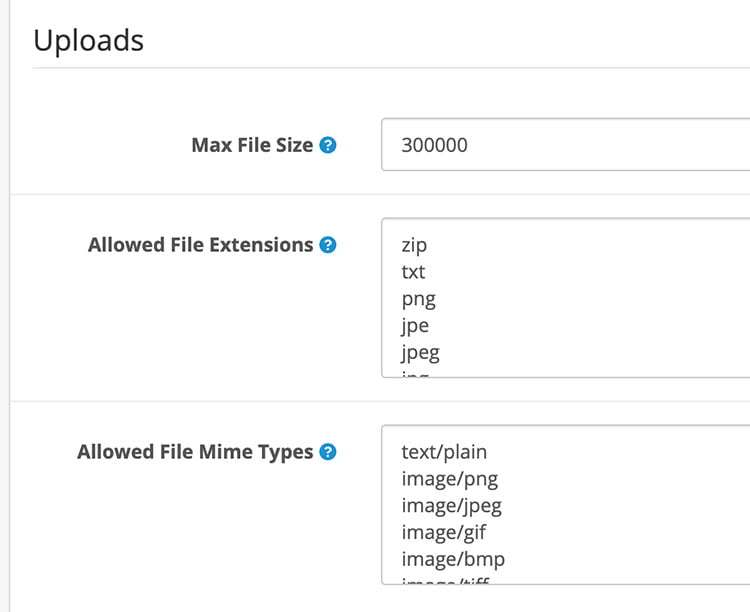
Allowed File Extensions: Add which file extensions are allowed to be uploaded. Use a new line for each value.
zip txt png jpe jpeg jpg gif bmp ico tiff tif svg svgz zip rar msi cab mp3 qt mov pdf psd ai eps ps doc
Allowed File Mime type: Add which file mime types are allowed to be uploaded. Use a new line for each value.
text/plain image/png image/jpeg image/gif image/bmp image/tiff image/svg+xml application/zip "application/zip" application/x-zip "application/x-zip" application/x-zip-compressed "application/x-zip-compressed" application/rar "application/rar" application/x-rar "application/x-rar" application/x-rar-compressed "application/x-rar-compressed" application/octet-stream "application/octet-stream" audio/mpeg video/quicktime application/pdf
Be sure there are no PHP and JS. In this way, you can secure your file upload buttons.
Review All Users, User group and Grant the Minimum Permissions Necessary
Go to admin >> System >> Users and see all users and verify what user group is assigned. Then check all User groups and see what access permission and modification permissions are given. Try to grant the minimum permissions as necessary. In Opencart you can make as many User groups as you want.
Use a strong username and password
Set a strong password. Better not to use admin as a username.
Opencart V3 has Max Login Attempts
Maximum login attempts are allowed before the account is locked for 1 hour. Customer and affiliate accounts can be unlocked on the customer or affiliate admin pages.
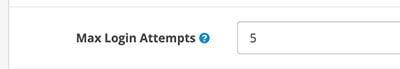
It is available only on Opencart v3 but you can implement this by following the tutorials at https://forum.opencart.com/viewtopic.php?t=218405#p790296
Two-factor Authentication free module
You can use this free two-factor authentication.
https://www.opencart.com/index.php?route=marketplace/extension/info&extension_id=32882
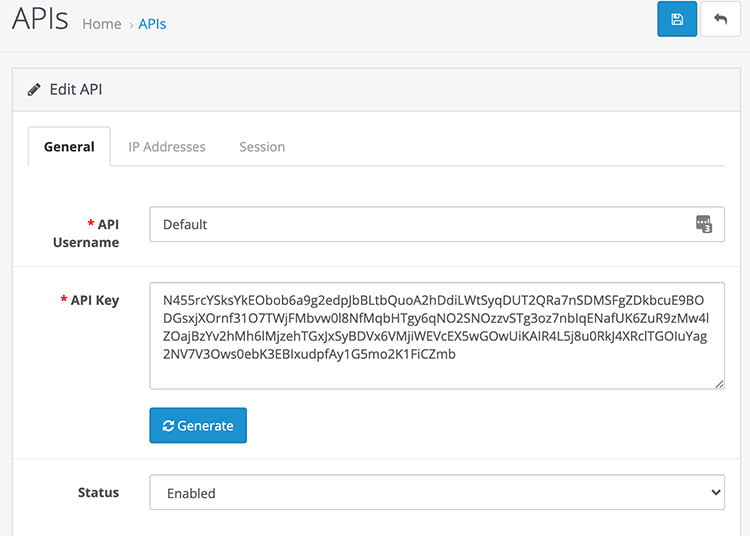
API security in Opencart
Similarly, check your API access as well. Go to admin >> System >> Users >> API and review all your API usernames and set proper API usernames, API keys, and IP addresses.
Always use the latest Opencart version, theme, modules, and extensions
It is better to use the latest Opencart version, theme, modules, and extensions. You may get problems getting the upgraded version of your custom modules and extensions but if you don’t update it then you risk the security.
Remove unused modules or extensions
Login to admin >> Extensions >> Installer >> you can see a list of modules that are installed. Remove unused modules or extensions. Similarly verify if old files and folders are remaining, especially for custom modules and themes.
Don’t use nulled Opencart theme or modules or extensions
Choose trustworthy plugins and theme providers, it can cost you some but it will protect you a lot.
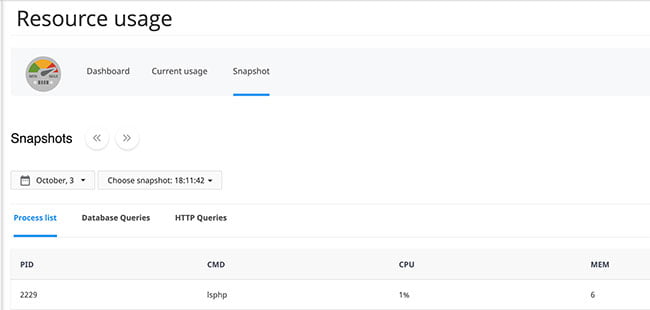
Monitor your server logs as well
If you are using CPanel hosting then you can check the Resources Usage at Login to Cpanel >> Metrics >> Resources Usage >> Snapshots. You can check that resource limits are being reached, resulting in slow performance or errors. Often resource issues are due to scripting/plugins on your site, development work such as making changes, or an increased amount of traffic. You and your web developer can review the resource usage of your account and take steps to reduce the load. Some scripts which are running long by some IP address means there is some fishy going on, so make sure to keep on checking it and see if you can improve your code and scripts.
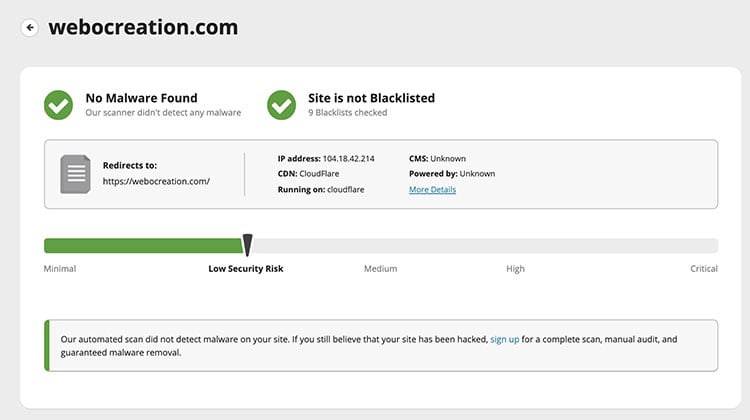
Free Opencart website security check & malware scanner
You can check your website security and malware at https://sitecheck.sucuri.net/
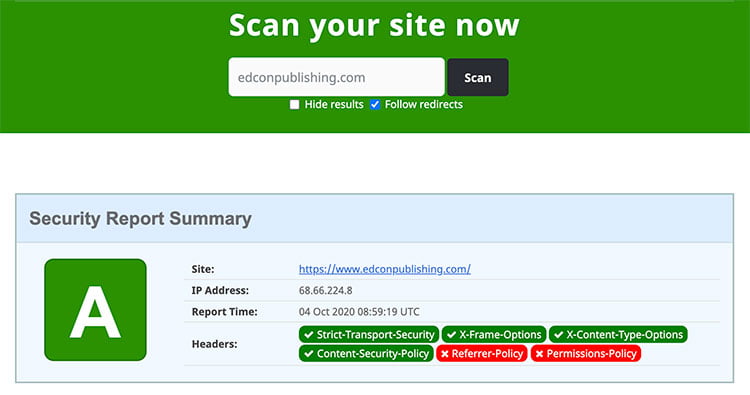
Use HTTP security headers
You can get your HTTP security headers to report at https://securityheaders.com/
Cross-Site Scripting (XSS)
If the programmer is tricky then in Opencart it is easy to add the JS script which may easily cause Cross-Site Scripting. Cross-Site Scripting (XSS) is when a malicious script is injected into a trusted website or application. The attacker uses this to send malicious code, typically browser-side scripts, to the end-user without them knowing it. The purpose is usually to grab cookies or session data or perhaps even rewrite HTML on a page. Go to admin>> Extensions >> Extensions >> Choose the Extensions Type as “Analytics” and see in the Google Analytics code field, if only required JS codes are added. If you see suspicious JS code then better to remove it.
Database Security and SQL Injections
Always use a strong database username and strong password. You can check this at config.php and admin/config.php, if you don’t have then you need to change to a strong password and username.
Similarly, if you are using custom modules and there are database queries then you need to verify whether the queries are written properly, whether all the fields are escaped properly or not and so.
One example of how they can inject the extra queries if you don’t escape the fields is below:
YOUR_OTHER_QUERIES_customerid=0&directory=%2Febooks%2F1115.pdf&model=1115%27%2F%2A%2A%2FAND%2F%2A%2A%2FEXTRACTVALUE%282030%2CCONCAT%280x5c%2C0x4c634d6c%2C%28SELECT%2F%2A%2A%2FMID%28%28IFNULL%28CAST%28email%2F%2A%2A%2FAS%2F%2A%2A%2FNCHAR%29%2C0x20%29%29%2C1%2C22%29%2F%2A%2A%2FFROM%2F%2A%2A%60.%%60%2F%2A%2A%%2F%2A%2A%2FBY%2F%2A%2A%2F%%60%2F%2A%2A%2FLIMIT%2F%2A%2A%2F8570%2C1%29%2C0x4c634d6c%29%29%2F%2A%2A%2FAND%2F%2A%2A%2F%276538%27%3D%276538&modelfinal=EREM+1115&order_id=30572&product_id=3389
See that bold section in the above queries, another query is concatenated and SQL injected is done.
Denial of Service
This is the most dangerous vulnerability, Denial of Service (DoS) exploits errors and bugs in the code to overwhelm the memory of website operating systems. Hackers have compromised millions of websites and raked in millions of dollars by exploiting outdated and buggy versions of Opencart software with DoS attacks. The hackers keep on running the code and your server CPU usage will be 100%, your server’s Physical Memory Usage is full and the website will not be available for real users or customers.
One of the best recommendations is to use a reputable 3rd party security service like Cloudflare or Sucuri and be sure to use the code and scripts properly.
Back up
Be sure to make as much backup as possible.
Use Google Captcha or Basic Captcha
Using Google Captcha or basic captcha on the form also helps you remove spam and get emails that contain vulnerable links.
These are some of the securities cheat sheets for Opencart. Please let us know if you are using any other tactics to make the Opencart website secure. Hope you liked this article, please subscribe to our YouTube Channel for Opencart video tutorials. You can also find us on Twitter and Facebook. Happy learning.





Well, advising People to always ue the latest OpenCart Version might not be the best advise, since latest OC Versions are also known to usually still have many flaws and unsolved yet Problems.
Well, advising People to always ue the latest OpenCart Version might not be the best advise, since latest OC Versions are also known to usually still have many flaws and unsolved yet Problems.
great post